
Sycor.ZeroTrust -
The IT Security Model of the Future
What does Zero Trust mean?
Zero Trust is a security concept that meets today's requirements for IT infrastructures - consisting of hybrid sourcing variants and the demand to be accessible remotely from anywhere at any time. It is not individual network areas that are protected; instead, access request of an identity has to be verified, no matter from which device or via which connection the user tries to access certain company resources. Authentication is based on identity- and role-based access rights via a hybrid Active Directory.
Structure of the Sycor.Zero Trust Security Model
Zero Trust is based on the principle: Nothing is safe! This means that every request from your own network is checked as if it came from outside. No distinction is made between the target and the benefit of the request. Each request to the network is thus verified before each access, provided with corrections and then encrypted again. The process is supported by microsegmentation. In addition, analytics and business intelligence systems protect by constantly monitoring the processes, detecting deviations and blocking suspicious activities if necessary.
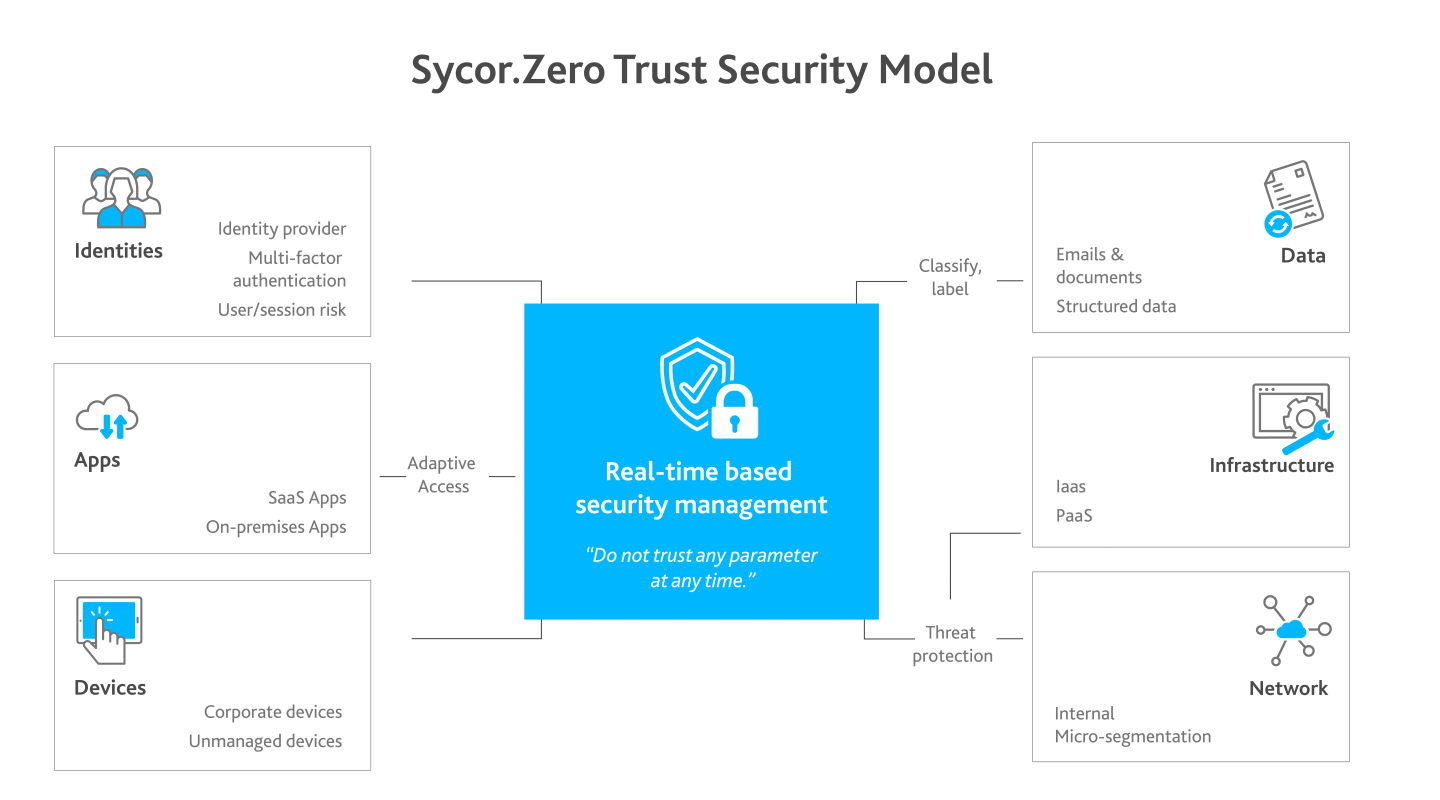
What are the components of a Zero Trust model?
Identities
Identity recognition should be secured by high verification procedures.
End devices
Get an overview of all company devices. This creates the basis for checking each device for trustworthiness and compliance before each access.
Networks
The internal network is often overlooked. Constantly protect it, too, with encryption, access permissions, and microsegmentation.
Data
The data-driven Zero Trust principle replaces perimeter-based security models. This is supported by business intelligence and corporate policies that limit access rights.
Infrastructure
Your infrastructure should be based on granting each user only the most necessary access rights. Evaluate access to your systems through telemetry and record irregularities in user behavior.
Apps
Create an authorization system for all applications and users in your company. Adjust the respective usage per user according to the tasks. Here, the principle applies that each user receives only the most necessary authorizations.
Holistic strategy and comprehensive consulting
Companies need a comprehensive, long-term resilience strategy and an associated zero-trust strategy. However, this is not something that can be implemented in a time-limited IT project. This is because the concerns of all areas of the company whose work is based in some way on IT infrastructure must be included - a strategic ongoing task that will accompany companies on their path to digitalization. Start planning and choose the approach that best fits your situation and goals.
These blog posts might also interest you
Your contact
Sycor stands by its customers as an experienced partner. We have extensive expert knowledge from more than 20 years of IT projects and operational experience.
Learn more about Sycor.ZeroTrust and contact us.

Our partners
All partners








